An IDS (Couldn't find Snort on github when I wanted to fork) - eldondev/Snort. Following is the stepwise procedure for installation and configuration of NetBus 2.0 Pro (server and client). 1) Download NetBus 2.0 Pro. From here - NB2ProBeta.zip. 2) Extract and install properly on your system. 3) After installation you will find the two shortcuts in the NetBus installation directory.
There are several things that come to mind when talk of the 1990’s comes around. Nirvana, vodka, cheap rap, and well- global warming wasn’t the subject of every conversation. But what really outshines the rest is the world of computing. The world of security was just getting its foothold into what is now a highly evolved and much more complicated scene. Three programs in particular allowed anyone to pull of amazing feats of prowess- all without any hacking knowledge.
Today these programs won’t make it past a cheap firewall. And we can’t recommend pranking a friend, but if you do, make sure he has his back turned at least long enough for you to turn his firewall off. Or if you’re clever with words, you might convince him to do it himself!
Back Orifice / Back Orifice 2000
Back Orifice, or BO, is one of the more common backdoor programs- and one of the most lethal of the bunch. The name may seem like a joke, but rest assured, the threat was quite real for its time. Back Orifice was created by the Cult of the Dead Cow group. If you haven’t noticed, they seem to have a knack for a sense of off-the-wall humor. Aside from the bizarre name, the program commonly runs on port 31337- a reference to the “Leet” phenomenon popular among hackers.
Pictured above is Back Orifice Version 2000. Back Orifice uses the client-server model, whereas the server is the victim and the client is the attacker. What made Back Orifice so dangerous is that it can install and operate silently. There is no need for user interaction whatsoever, meaning you could have it on your computer even today and not be aware of it.
Companies such as Symantec have taken steps in guarding computers against the program, as they have deemed it as dangerous. This is due partly to the fact that it is still being actively developed as an open source tool. As stated in the BO documentation, the goal is to ultimately make the presence of Black Orifice 2000 unknown- even to those who installed it.
Back Orifice 2000 is being developed for Windows 95, Windows 98, Windows NT, Windows 2000, and Windows XP.

Where Can I Download Back Orifice 2000?
Back Orifice 2000 may be downloaded at the following location: http://sourceforge.net/projects/bo2k/
Removal of Back Orifice 2000 will require that you edit your registry settings. To remove it in 7 easy steps, refer to the diagram below.
How To Remove Back Orifice 2000
- 1. Click Start > Run, and then type “Regedit” (without quotes)
- 2. Follow the below path: “HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRunServices”
- 3. Now in the right window, look for the following: “umgr32 = ‘c:windowssystemumgr32.exe”
- 4. Right click on this entry, and click delete. Now restart your computer.
- 5.After the restart, only open Windows Explorer. Make sure you can see all registered extensions. To do so, go to View > Options, and configure the appropriate settings.
- 6.Go to the WINDOWSSYSTEM directory, and find the “umgr32.exe” file. Once you’ve found it, delete it.
- 7. Exit Windows Explorer and restart your computer once more.
NetBus / Netbus 2.0 Pro
NetBus was created around the same time that Back Orifice was- the late 1990’s. NetBus was originally designed as a program to prank friends and family with- certainly nothing too malicious. The program made its debut in 1998, making pranks and attacks still available in the later 1990’s.
What makes NetBus famous is that in 1999, a law scholar by the name of Magnuss Eriksson was a victim of a NetBus attack. Child pornography was placed on his computer, coworkers found it, and he lost his job. Only 5 years later did he reclaim his innocence, but after much turmoil and emotional treatment. Some pranks go a little too far, as you can tell.
Where can I Buy and Download NetBus?
NetBus may be bought and downloaded at the following location: http://www.netbus.org/
Luckily, the latest version of NetBus is a valid program. It can be removed just like any other program. Previous releases of NetBus are a little more difficult, however.
How To Remove NetBus
- 1. Click Start > Run, and then type “Regedit” (without quotes)
- 2.Follow the below path: “HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRunServices”
- 3. Now in the right window, look for the following: “[Name_of_Server].exe” Of course, you will have to find the actual name of the exe file. It is commonly “Patch.exe” or “SysEdit.exe”, but may differ.
- 4.Restart, and remove any traces of the actual program that may be left. Optionally, you may Install NetBus yourself, and then use its own removal feature.
SubSeven / Sub7
SubSeven, or Sub7, was created for the same purpose NetBus was- for pranks. Sub7 actually has support for more pranks and also has a better looking user interface.
Where can I Buy and Download Sub7?
Sub7 is not supported anymore, and thus, is not available for download on any legit websites. If you were to do a Google search, you would find links to download Sub7. However, these are not official sites, and should be considered shady or dangerous.
How To Remove Sub7
- 1. End the following processes via task manager: ”editserver.exe, subseven.exe”
- 2.Remove the following files: “editserver.exe, subseven.exe, tutorial.txt.”
Why These Programs Are Completely Legal
The entire basis behind these programs is that they are designed to help people- not do harm. While some such as NetBus were indeed originally created for pranks, they have switched routes to avoid legal troubles.
These programs claim to be legit remote desktop programs, although they are obviously easily used for malicious use. These programs are actually supposed to be used for helpdesk or customer support departments. Why every pre-teen of the1990’s had a copy is beyond us, but we get the feeling these were being used for more than testing purpose.
The advent of newer technology has made these programs in some ways less effective. However, programs such as Back Orifice 2000 are still yet evolving. The Back Orifice team has also been rumored to be working on a sequel to their program- will it impact computing the same way the late 1990’s were with these programs?
For our own entertainment purposes, we can only hope.
Photo Attribution: emailmks Flickr via Compfightcc
NetBus was written in Delphi by Carl-Fredrik Neikter, a Swedish programmer in March 1998.It is capable of :--
* Open/Close CD-ROM
* Show optional BMP/JPG image
* Swap mouse buttons
* Start optional application
* Play a wav file
 * Control mouse
* Control mouse* Show different kind's of messages
* Shut down Windows
* Download/Upload/Delete files
* Go to an optional URL
* Send keystrokes and disable keys
* Listen for and send keystrokes
* Take a screendump
* Increase and decrease the sound-volume
* Record sounds from the microphone
* Make click sounds every time a key is pressed

This utility also has the ability to scan 'Class C' addresses by adding '+Number of ports' to the end of the target address. Example: 255.255.255.1+254 will scan 255.255.255.1 through 255.
NetBus 2.0 Pro :- It was completely re-written and re-designed. It now has increased features such as improved GUI for client and server, improved file manager, windows manager, registry manager, plugin manager, capture of web cam images, n...more............!
Following is the stepwise procedure for installation and configuration of NetBus 2.0 Pro (server and client).
1) Download NetBus 2.0 Pro. from here - NB2ProBeta.zip
2) Extract and install properly on your system.
3) After installation you will find the two shortcuts in the NetBus installation directory.
This is to be executed on victim's system.
This is to be executed on your system.
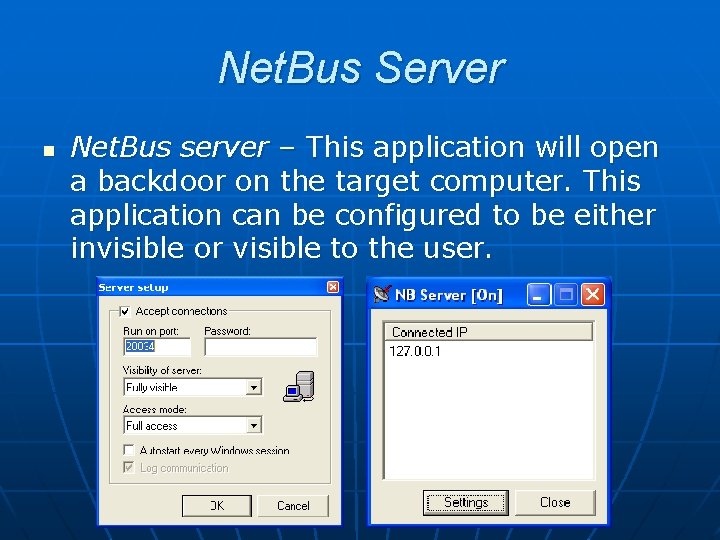
4) By Executing the 'NetBus Server' (on victim's computer), you will be greeted by a window as shown in figure (left). Click on 'Settings' button.
Here you can configure server settings such as port no, password, visibility, auto/manual start, etc. as shown in figure (right).
Click on 'OK' button to finish NetBus Server settings.
Then close the NetBus Server window.
Netbus 2 0 Server And Client Software List
5) By executing 'NetBus' (i.e. client)(on your system), you will be greeted by a window as shown below-Netbus 2 0 Server And Client Software Update
6) To add a new host go to the menu 'Host' and then click 'New'. This is as shown in figure (left).Here you should enter the proper Destination(e.g. 'My Computer'), IP Address(eg. 72.232.50.186), TCP Port(by default 20034), Username/Password(exactly same as that of 'NetBus Server') for target computer.
Click on 'OK' to finish the addition of new host.
Netbus 2 0 Server And Client Software Update
7) Now you are ready to connect with target(victim's) computer.Netbus 2 0 Server And Client Software Download
Netbus 2 0 Server And Client Software
 To do so, select the host from main window then go to 'Host' menu and then click 'Connect'.
To do so, select the host from main window then go to 'Host' menu and then click 'Connect'.8) After client get connected with server(target computer), you can use any of the features of 'NetBus Trojan' as listed above. You can see all these tools on 'Toolbar' of NetBus Client.